5 Benefits of Cyber Threat Intelligence
With the increasing rise in cyber threats, all businesses and institutions need to equip themselves with strong defenses. Cyber Threat Intelligence (CTI) is one such weapon that is becoming more and more popular.
A lot of companies that sell cybersecurity are using cyber threat intelligence due to its numerous benefits. Not only does it help detect existing threats, but threat intelligence also helps to predict future threats' nature and sources and empowers organizations to implement risk management policies.
This article explores the many advantages of cyber threat intelligence and explains its place in cybersecurity.
What is Cyber Threat Intelligence?
Cyber threat intelligence is data that is gathered, examined, and processed to comprehend the objectives, targets, and attack patterns of a cyber threat. By using cyber threat intelligence, organizations can become more proactive in their efforts to mitigate cyber attacks and make data-driven, quicker, and more informed security decisions.
According to an article by IBM, the process of CTI happens in two steps. Firstly, raw threat and security-related data from many sources are collected and compiled, and then security analysts correlate and analyze the information to find patterns, trends, and linkages that offer a comprehensive picture of the real or possible dangers of the cyber attack.
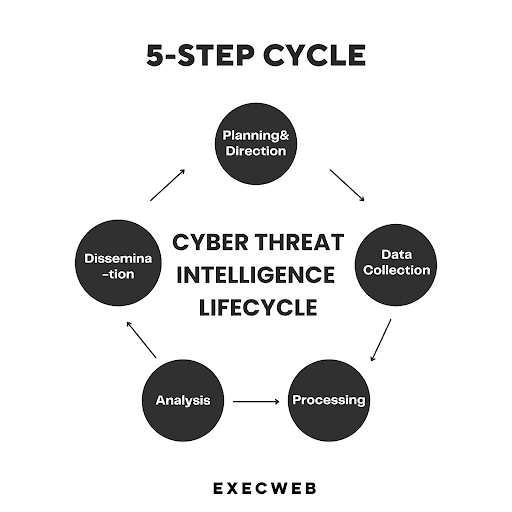
Cyber Threat Intelligence Life Cycle
Cyber threat intelligence is not a single-step process but consists of five to six steps to turn raw data into intelligence.
1. Planning & Direction
During the planning and direction phase of the cyber threat intelligence cycle, CISOs or security officers take a proactive approach to set clear objectives for their intelligence programs. They carefully assess the organization's risk landscape, identify critical business processes, and determine the sensitive data that requires protection. This stage involves strategic decision-making, resource allocation, and establishing a roadmap for the entire intelligence program.
2. Data Collection
In the data collection phase, diverse sources are tapped into to gather relevant information. This includes in-house threat intelligence generated from security monitoring systems, collaboration with industry vertical communities, monitoring of dark web channels, and leveraging open-source feeds. The aim is to cast a wide net to capture indicators of compromise, vulnerabilities, threat actors' activities, and emerging trends in the cyber threat landscape.
3. Processing
Once the data is collected, it needs to be processed to make it more manageable and standardized. This involves organizing, categorizing, and structuring the raw data into a specific format that can be easily analyzed and compared. Processing also includes data enrichment by incorporating additional context, such as threat intelligence feeds, geolocation data, or historical patterns. The processed data becomes a foundation for subsequent analysis.
4. Analysis
In the analysis phase, skilled professionals dive deep into the processed data to uncover valuable insights. They apply various analytical techniques and tools to identify patterns, correlations, and potential threats. This includes identifying commonalities among indicators, connecting disparate pieces of information, and detecting emerging trends or attack methodologies. The analysis helps to prioritize threats, understand adversaries' tactics, and develop effective data protection strategies and response plans
5. Dissemination
The final stage of the cyber threat intelligence cycle involves disseminating the analyzed intelligence to the relevant stakeholders within the organization. This typically includes executives, security teams, incident response teams, and other key decision-makers. The intelligence is presented in a meaningful and actionable format, such as reports, dashboards, or threat briefings. The dissemination process ensures that the intelligence is effectively communicated, enabling informed decision-making, proactive defense measures, and the allocation of appropriate resources to mitigate risks.
Why Cyber Threat Intelligence Is Important
Businesses of all types, whether they are involved in cybersecurity or not, are facing security challenges. It seems like a never-ending battle as hackers come up with new techniques to breach networks and steal sensitive data. Most businesses don’t have enough time and resources to sift through a mountain of data to find anomalies and false alarms.
The main goal of Cyber Threat Intelligence is to help enterprises be proactive and predictive to detect all the potential vulnerabilities in IT infrastructures. It helps cybersecurity professionals and businesses to understand which types of vulnerabilities can act as entry points for cybercriminals so they can build defense frameworks and strategies accordingly. Thus, your organization will have better visibility of the cyber attacks that may attack their IT systems.
5 Benefits of Cyber Threat Intelligence
1. Provides Operational Intelligence
Operational Intelligence or technical Cyber Intelligence provides highly-focused and technical intelligence to give time warnings and provides support and guidance to respond to specific cyber incidents.
CTI assesses specific and potential cyber incidents happening around to form an overall picture of the intent and capabilities of malicious cyber attacks. It helps identify trends, emerging threats, and attacking patterns to provide policymakers with important information including the malicious actors, tools, and sources so they can develop a timely secure mechanism.
Operational intelligence also leads to the following cyber threat intelligence benefits:
- Increases situational awareness: Operational intelligence can help organizations increase their situational awareness by providing them with information about the current state of the threat landscape. This information can be used to make better decisions about how to allocate resources and prioritize security initiatives.
- Improves threat hunting: Operational intelligence can help organizations improve their threat hunting capabilities by providing them with information about the tactics, techniques, and procedures (TTPs) of known threat actors. This information can be used to identify and investigate potential threats before they cause damage.
- Reduces response time: Operational intelligence can help organizations reduce their response time to incidents by providing them with information about the nature of the incident and the potential impact. This information can be used to quickly deploy resources and take action to mitigate the damage.
- Improves collaboration: Operational intelligence can help organizations collaborate with each other to share information and best practices. This collaboration can help to improve the overall security posture of the community.
2. Improved Situational Awareness
Cyber threat intelligence fosters improved situational awareness by providing organizations with a thorough grasp of the threat they might face, Organizations may learn about new threats and changing attack vectors by tracking and evaluating threat data from a variety of sources, such as malware repositories, dark web forums, and open-source intelligence. By taking a proactive approach, defenses may be strengthened before an attack happens.
3. Cost-Effective
Cyber threat intelligence might sound like a huge investment but it’s cost-effective and will save your enterprise from huge financial losses. A small data breach can cost your business $8 million along with lawsuits, fees, penalties, and a massive decline in sales due to a loss of trust among customers.
Cyber threat intelligence can save you from such heavy costs, both in terms of monetary and reputation, and help you develop a plan of action to prevent cyber attacks.
4. Improves Performance of Your Defense Team
Cyber threat intelligence makes your defense team incredibly more efficient and saves them from alert fatigue and burnout. Monitoring and correlating cyber attacks can be resource-intensive and time-consuming.
The latest CTI technology uses artificial intelligence and security information to collect and correlate important data and help security teams to identify threats immediately. By integrating such intelligence into your IT infrastructures, your security teams will be able to cut down on false positives and focus on what really matters.
5. Investing In The Right IT Infrastructure
Cyber threat intelligence not only helps your defense team to monitor and detect the looming threat more efficiently but also ensures your infrastructure is advanced enough to address these attack vectors.
When your security team understands the cyber threat landscape, they will be able to identify the threats that might target your business. In this way, you will know which technologies you’ll need to invest in to protect your business. For that, executives and stakeholders of an organization must ensure consistent communication to discuss threats and align overall security objectives.
6. Protection of Intellectual Property
Protection of Intellectual property is a key component of competitive advantage for many organizations. CTI is essential to protecting this intellectual property because it offers insights into cyber attacks designed to steal or compromise sensitive information. Organizations may put strong defenses in place to prevent their private data from ending up in the wrong hands by keeping an eye out for signs of intellectual property theft and corporate espionage. This strategy protects the organization's competitive advantage in the market.
7. Collaborative Knowledge
The cyber threat intelligence process enables sharing of important practices and information about cybersecurity threats across the organization. By sharing the information, it keeps all the employees aware of the possible threats.
From top to bottom, cyber threat intelligence benefits each member of the security team including:
- SOC
- CSIRT
- Intel Analyst
- Sec/IT Analysts
- Executive Management
In this way, companies can also share tips and practices with their employees to ensure everyone is aware of the cybercriminals' patterns and everyone is on the same page against the threat actors.
How to Create a Cyber Threat Intelligence Program?
The Cyber Threat Intelligence program consolidates numerous Threat Intelligence Feeds into a unified feed, rather than assessing them individually. This integration facilitates uniform characterization and categorization of cyber threat events, aiding in the recognition of trends or alterations in the behavior of cyber adversaries. By consistently outlining cyber threat activity, the program promotes streamlined information sharing and facilitates threat analysis. Additionally, it supports the threat intelligence team by cross-referencing the feed with internal telemetry data and generating alerts as necessary.
Learn how to create a threat intelligence function in this insightful video.
Conclusion
In this digital age where organizations are facing cyber attacks from left, right and center, cyber threat intelligence has become a necessity. The countless benefits to the organizations from risk management, to regular compliance, staffing efficiency, and allocating capital in the right infrastructure make CTI a worthwhile investment. That’s why more and more businesses are investing in this technology.
If you’re a company that sells cybersecurity services, know that cybersecurity solutions are effective only when CTI empowers them. If you want to learn more about CISOs' demands for cybersecurity solutions, join Execweb today which is a cybersecurity executive network. Here you will find an opportunity to contact relevant CISOs, CIOs, and other security professionals through virtual roundtables and learn more about the latest cybersecurity trends.








Comment